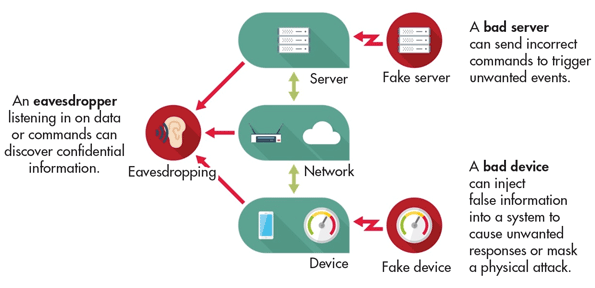
Security, therefore, will ultimately be the limiting factor on how much IoT technology is deployed. With security, the traditional trade-off is either “easy to use” or “secure”— but not both. We often consider a third tradeoff, as well, features; in most cases, operators are not willing to trade off features, but it is certainly part of the equation. An operator striving for an Industrial IoT (IIoT) network must look at SCADA security, the convergence of Operations Technology (OT) and Information Technology (IT), and make a thorough assessment of what will allow them to achieve a secure data communications network and where they want to be in this triangle.
Source: Security Considerations for IIoT Challenge | SCADA, IT, OT and Beyond



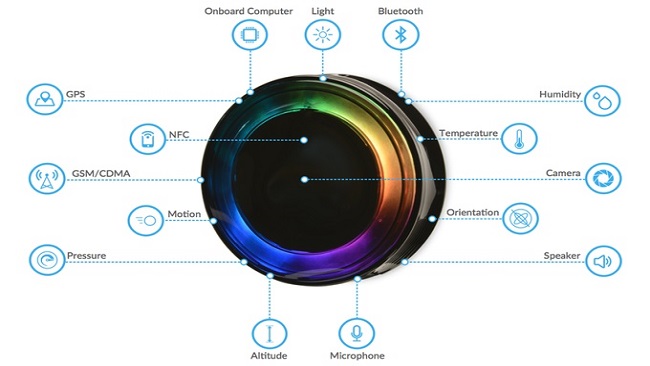 The computer vision technology uses facial, emotion, vehicle, and crowd analysis to track real-time engagement with advertising campaigns, analyze store layout and customer flow for optimized point-of-sale (POS) efficiency, and gather business intelligence (BI) data. Saccoman said the start-up’s experience with hardware product development and open-source software through AdBeacon helped prepare AdMobilize to design MATRIX for business applicability and with a developer-focused mindset. He described AdBeacons as “Google Analytics for the physical world.”
The computer vision technology uses facial, emotion, vehicle, and crowd analysis to track real-time engagement with advertising campaigns, analyze store layout and customer flow for optimized point-of-sale (POS) efficiency, and gather business intelligence (BI) data. Saccoman said the start-up’s experience with hardware product development and open-source software through AdBeacon helped prepare AdMobilize to design MATRIX for business applicability and with a developer-focused mindset. He described AdBeacons as “Google Analytics for the physical world.”