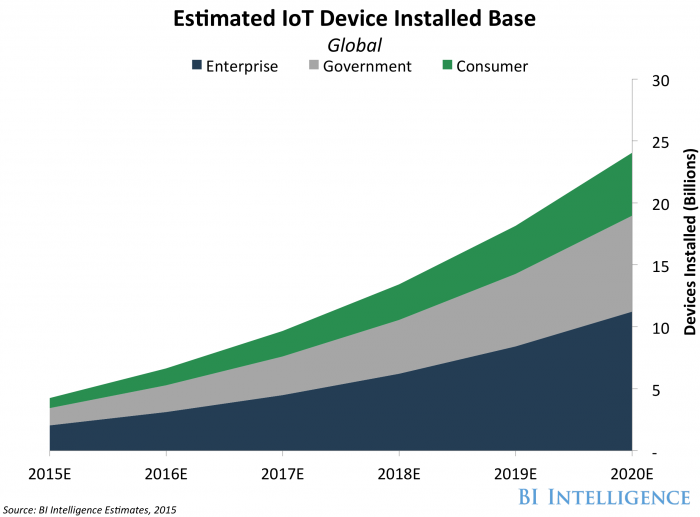
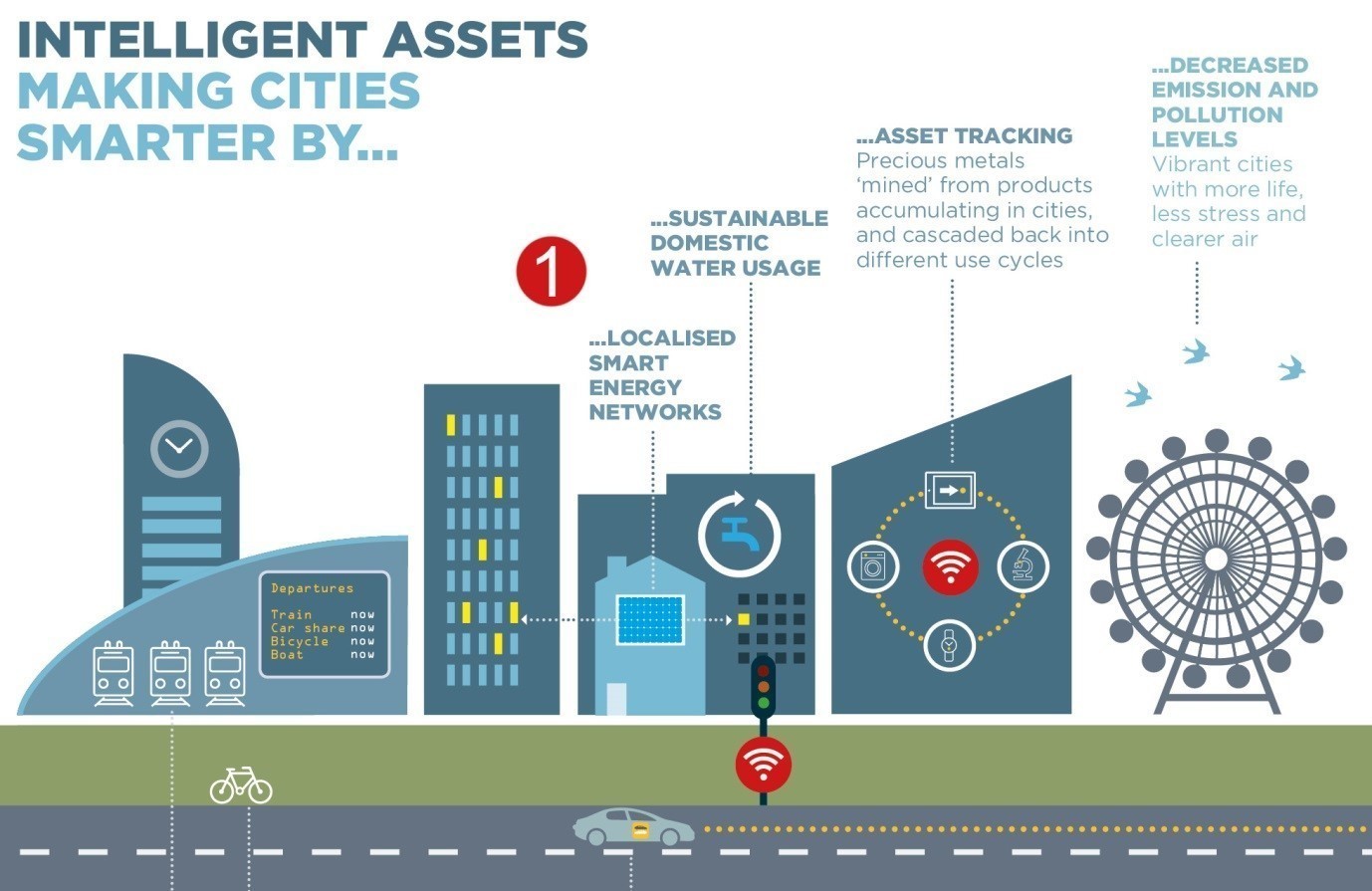
Industrial control systems (ICS) are just as critical to daily life yet cyber protections aren’t always built in, particularly when it comes to decades-old legacy systems. As a result, the need to maintain these older systems is critical. They also don’t have unique identification numbers to help manufacturers alert industrial organizations of new vulnerabilities or recommended upgrades. Without the ICS, operations in utilities and oil and gas would come to a halt, yet new research from RSA revealed energy organizations, alongside government, ranked lowest in cyber maturity, with only 18 percent of respondents classifying as developed or advantaged. Further, incident response (IR) capabilities were reported to be either “ad hoc” or “nonexistent.”.
Source: 3 Steps Towards Building Cyber Resilience Into Critical Infrastructure | Dark Reading